
For Christmas, the Department of Defense (DoD) asked the Defense Industrial Base (DIB) for a shiny new $63 billion Cybersecurity Maturity Model Certification (CMMC) Program. The anxiously awaited CMMC Rule was published in the Federal Register for public comment the week of Christmas 2023, with comments due by February 26, 2024. This proposed rule is the second attempt by the DoD to publish a CMMC regulation to implement the CMMC program officially. In September 2020, the DoD attempted to implement CMMC through an interim final rule; however, that effort was stalled primarily due to the change in presidential administrations, the transfer of the CMMC program from the office of the Undersecretary of Defense for Acquisition and Sustainment (USD(A&S)) to the office DoD CIO (Chief Information Officer), and an investigation into the chief CMMC Program architect for allegedly mishandling classified information.
This time around, the DoD plans to publish two CMMC Rules, one in 32 C.F.R. Section 170 to define and describe the CMMC program and a second in the Defense Federal Acquisition Regulation Supplement (DFARS) in Part 48 of the C.F.R. which will be used to incorporate the CMMC requirements into DoD contracts. Only the 32 C.F.R. Section 170 rule is available for public comment.
Overview of CUI and the CMMC Program
Controlled Unclassified Information (CUI) is generated by, for, or on behalf of the Executive Branch of the U.S. Federal Government. CUI is sensitive but unclassified information. Federal agencies designate specific types of information as CUI based on laws, regulations, or Government-wide policies, and the National Archives and Records Administration (NARA) maintains the only authoritative registry of CUI categories. Only information that falls into a CUI category and is produced by the Government or by a contractor performing work under a government contract can be designated as CUI.
Federal regulations require contractors to use NIST SP 800–171 when establishing security requirements to protect CUI’s confidentiality on contractor-owned, non-Federal, information systems. Before the creation of the CMMC Program (and while CMMC is still going through the rulemaking process) DoD requires contractor self-attestations of compliance to NIST SP 800-171. However, the DoD no longer believes that self-attestation is sufficient to ensure the protection of DoD CUI. At its core, the CMMC Program is a third-party assessment scheme to validate contractor implementation of the NIST SP 800-171 security controls on contractor-owned, non-Federal, information systems. The DoD seeks to establish CMMC as a pre-award requirement that will demonstrate to DoD procurement officers the contractor’s ability to protect DoD CUI adequately.
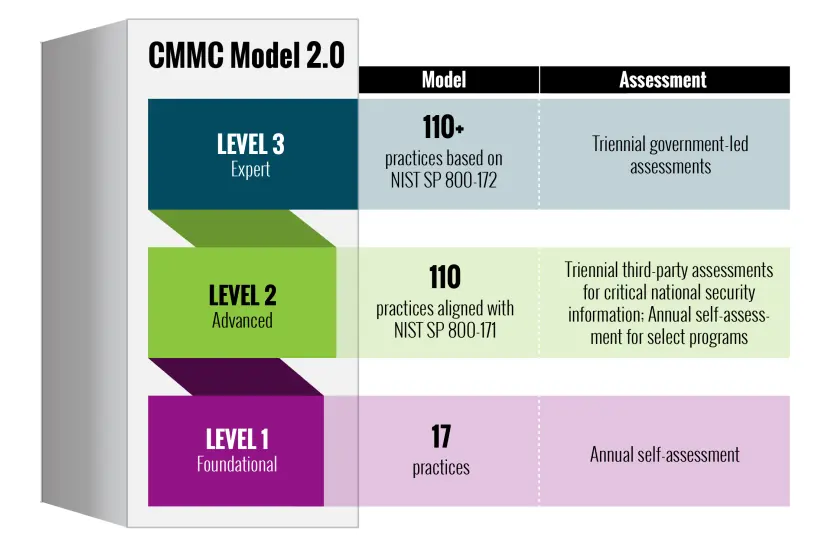
The CMMC scheme establishes three levels of requirements, Levels 1, 2, and 3:
- CMMC Level 1:
- Required for organizations that do not handle CUI
- Requires contractors to implement 15 security requirements currently required by the FAR clause 52.204-21
- Requires annual self-assessment of the 15 security requirements
- CMMC Level 2:
- Minimum level required for handling DoD CUI
- Requires contractors to implement the 110 security requirements currently required by DFARS clause 252.204-7012, which are aligned to NIST SP 800-171
- Requires either an annual self-assessment or third-party assessment of the security requirements in NIST SP 800-171 every three years
- CMMC Level 3:
- The circumstances under which DoD will require Level 3 have not been established
- To comply, contractors must implement the 110 NIST SP 800-171 security requirements plus 24 selected requirements from NIST SP 800-172
- Requires a CMMC Level 2 third-party assessment of the 110 NIST SP 800-171 controls plus a CMMC Level 3 DoD-led assessment of the 24 NIST SP 800-172 controls
The DoD Program Managers or requiring activities will determine which CMMC Level will apply to a contract or procurement.
Source: DoD CIO CMMC website
The CMMC ecosystem is comprised of:
- DoD CMMC Project Management Office (PMO):
- Located within the Office of the DoD CIO (Chief Information Officer)
- Provides oversight of the Accreditation Body
- Responsible for developing, updating, maintaining, and publishing the CMMC Model, CMMC Assessment Guides, and policies for implementation of the CMMC Program
- DIBCAC (Defense Industrial Base Cybersecurity Assessment Center):
- Conducts CMMC Level 3 Certification Assessments of defense contractors
- Conducts CMMC Level 2 assessments of the Accreditation Body and C3PAOs
- CMMC Accreditation Body (CMMC AB d/b/a “Cyber AB”):
- Authorizes, accredits, and provides oversight of all third-party assessment companies, known as C3PAOs
- Not-for-profit private entity established in 2021
- Awarded a single-source, “no-cost,” 10-year contract with DoD to perform services as the CMMC AB
- C3PAO (CMMC Third-Party Assessment Organizations):
- Private entities
- Conduct CMMC Level 2 Certification Assessments
- CAICO (CMMC Assessor and Instructor Certification Organization):
- Trains, tests, authorizes, certifies, and recertifies CMMC assessors, instructors, and related practitioners
- Not-for-profit private entity, wholly owned by the CMMC AB
- Incorporated in 2022
CMMC Program Implementation and Costs
DoD plans to implement the new CMMC proposed rules over seven years in four phases, with the first phase starting as soon as the CMMC DFARS rule is finalized. While the DoD establishes implementation milestones across four phases in this rule, the rule text provides no insights into how the DoD will govern or monitor the CMMC program to determine program effectiveness and to stagger the implementation process. Once the CMMC DFARS rule is finalized, the DOD CIO will no longer have control of the implementation process.
DoD estimates that the CMMC program will cost more than $63 billion over 20 years, with more than 221,000 companies being impacted over the seven-year phase-in period. A Level 1 self-assessment is estimated to cost organizations roughly $5,000 annually, and Level 2 self-assessments are expected to cost organizations nearly $50,000 every three years. Level 2 third-party assessments are expected to cost between $35,000 and $53,000, depending on the organization’s size.
How Do The CMMC Attestation Requirements Create Even More Opportunities for Violations of the False Claims Act?
To comply with the proposed CMMC requirements, organizations must conduct the requisite CMMC assessments per CMMC Assessment Guides, and a “senior official” from the organization must also submit affirmation statements attesting to continual conformance, at least annually, in SPRS. The DoD does not specify what title a “senior official” must hold within an organization but says that the official must ensure the organization complies with CMMC requirements. An affirmation statement must be submitted in SPRS after every CMMC assessment, whether a self-assessment or a third-party assessment, after a plan of action and milestone (POA&M) closeout assessment (if necessary), and annually thereafter.
The affirmation statements submitted by senior officials attest that the organization has implemented, and will maintain implementation of, all applicable CMMC security requirements for all information systems within the identified CMMC assessment scope at the applicable CMMC Level. Changes to the scope of the CMMC boundary, through infrastructure modifications, expansion, or acquisition, for example, may violate the SPRS affirmation statement and require a new CMMC assessment. The CMMC certification and attestation are valid only for the original CMMC scope. DoD does not guide the type or size of scope modification or expansion that might trigger the need for a new CMMC assessment. Large-scale modernization or data migration efforts that include migrating data from an on-premises solution to the cloud could alter a CMMC assessment scope so that a new CMMC assessment might be required.
Contractors must ensure that all cloud products that process, transmit, or store DoD CUI have a FedRAMP Moderate (or higher) Authorization or is FedRAMP moderate “equivalent.” On January 2, 2024, the DoD CIO released a memo describing the requirements for contractors to demonstrate the FedRAMP equivalency of all cloud products and services that do not have a FedRAMP Moderate Authorization but handle DoD CUI. To be considered FedRAMP Moderate equivalent, cloud providers must have implemented 100% of the current FedRAMP moderate baseline of controls and successfully undergo an assessment by a FedRAMP-recognized assessment organization (3PAO). Defense contractors are responsible for reviewing supporting documentation from cloud providers to ensure FedRAMP requirements have been met and verify that the cloud provider has a sufficient incident response plan. It is up to the contractor to review and accept FedRAMP equivalency documentation for all non-FedRAMP authorized cloud products in which they store or process DoD CUI. When senior officials submit attestation statements in SPRS, they are also attesting that their organization has reviewed and accepted as sufficient the supporting documentation from all non-FedRAMP authorized cloud products and services that handle DoD CUI.
DoD contracts will not require the CMMC-specific requirements until both CMMC rules are finalized and published. However, contractors who handle CUI must implement NIST SP 800-171 security controls, conduct a self-assessment of those controls at least annually, and report self-assessment scores into SPRS. Additionally, because of the availability of C3PAOs, some prime contractors may require subcontractors to obtain CMMC certifications before the CMMC requirements appear in DoD contracts. Organizations should ensure they contract for a CMMC Level 2 certification from an authorized C3PAO from the Cyber AB marketplace because the DoD will not recognize assessments performed by any other entity.
As the new CMMC proposed rules get implemented, companies face a choice of how they obtain the necessary certification. What they cannot choose to do, however, is to ignore cybersecurity.
If you are aware of a company choosing to ignore its obligations to keep CUI or other protected data safe, we urge you to contact a cybersecurity fraud attorney with Bracker & Marcus LLC for a free consultation. Let us help you protect the country’s important, confidential data.
